 |
 |

2011 Invention Awards: A Better Mechanical Hand 
In The Workshop One of the inspirations for Mark Stark’s [below] invention was an artificial hand designed for NASA. “It was a challenge,” he says. “I thought, ‘I can do better than that.’" John B. Carnett
|
Vehicle Monitoring and Security System
|
|
A new survey of small business ERP projects sheds light on project success and failure. A new survey of small business ERP projects sheds light on project success and failure. The survey covers a variety of ERP-related issues; however, we will focus on several points with a direct bearing on the successful outcome of projects. In summary, the survey shows a substantial increase in over-budget and late projects, relative to the previous year. |
|
|
GREEN COMPUTING
Easy Ways to Go Green with Your Computer
|
The Art of Listening
 Listening is an art that when done well delivers tremendous benefits.The goal of listening well is to achieve communication.
|
|
Detailed Articles |
|
|
A Better Mechanical Hand .jpg)
Prosthetic hands typically come in three varieties: purely cosmetic models; hooks and other low-cost mechanical appendages that provide a limited range of motion; and electronic versions that better mimic natural hand movements yet can cost tens of thousands of dollars. Mark Stark’s prosthetic incorporates the best elements of each. Although its minimalist plastic assembly is nearly as light and inexpensive as a common steel hook, it looks and moves like a high-end electronic hand. Stark, who makes his living designing valves for dryers and other appliances, got into prosthetics in part to help his friend, Dave Vogt, who was born without a left hand. Stark’s creation is electronics-free, but its fingers each have three knuckles (two on the thumb) that bend separately to conform to anything the wearer grasps, including irregularly shaped objects that a hook can’t hold.  How It Works: The Stark Hand: The prosthetic hand attaches to a cable that runs from a shoulder harness worn by an amputee. A lever on the palm opens all five fingers at once, and separate cables in each finger and springs at each knuckle allow the fingers to close individually and bend around objects with a secure grip. Blanddesigns.co.uk In 2004, Stark constructed a proof-of-concept from hardware-store supplies and gave it to Vogt to try out. Within an hour, Vogt caught a ball left-handed for the first time in his life. Since then, he has helped Stark test and improve four more prototypes. Stark designed stronger, compact springs, re-engineered the fingers into a few easy-to-manufacture shapes, and set the thumb at a new angle to better replicate a real thumb. He also strengthened the joints in the hand against side impacts after Vogt broke a prosthetic knuckle when he hit something while swinging around on the dance floor. Vogt now wears the hand everywhere except to his job as a machinist, where he has to do heavy lifting for which a hook still works better. A more durable production version, which will use tougher plastics and sleeker parts, could be on the way as early as this winter. Edison Nation, a company that helps inventors develop their ideas, recently selected Stark’s hand for commercial development and is now in talks to license it to a major prosthetics manufacturer. Name: The Stark Hand Inventor: Mark Stark Time: 7 years Cost: $17,000–$18,000 Article Source |
|
|
Vehicle Monitoring and Security System What if the person traveling can be tracked and also secured in the case of an emergency?! Fantastic, isn’t it? Of course it is and here’s a system that functions as a tracking and a security system. It’s the VMSS. This system can deal with both pace and security. The VMSS (Vehicle Monitoring and Security System) is a GPS based vehicle tracking system that is used for security applications as well. The project uses two main underlying concepts. These are GPS (Global Positioning System) and GSM (Global System for Mobile Communication). The main application of this system in this context is tracking the vehicle to which the GPS is connected, giving the information about its position whenever required and for the security of each person travelling by the vehicle. This is done with the help of the GPS satellite and the GPS module attached to the vehicle which needs to be tracked. The GPS antenna present in the GPS module receives the information from the GPS satellite in NMEA (National Marine Electronics Association) format and thus it reveals the position information. This information got from the GPS antenna has to be sent to the Base station wherein it is decoded. For this we use GSM module which has an antenna too. Thus we have at the Base station; the complete data about the vehicle. INTRODUCTION: Of all the applications of GPS, Vehicle tracking and navigational systems have brought this technology to the day-to-day life of the common man. Today GPS fitted cars, ambulances, fleets and police vehicles are common sights on the roads of developed countries. Known by many names such as Automatic Vehicle Locating System (AVLS), Vehicle Tracking and Information System (VTIS), Mobile Asset Management System (MAMS), these systems offer an effective tool for improving the operational efficiency and utilization of the vehicles. GPS is used in the vehicles for both tracking and navigation. Tracking systems enable a base station to keep track of the vehicles without the intervention of the driver whereas navigation system helps the driver to reach the destination. Whether navigation system or tracking system, the architecture is more or less similar. The navigation system will have convenient, usually a graphic display for the driver which is not needed for the tracking system. Vehicle tracking systems combine a number of well-developed technologies. Let us briefly explain how VMSS works. In order to monitor the vehicle, it is equipped with a GPS-GSM VMSS system. It receives GPS signals from satellites, computes the location information, and then sends it to the control center. With the vehicle location information, the control center displays all of the vehicle positions on an electronic map in order to easily monitor and control their routes. Besides tracking control, the control center can also maintain wireless communication with the GPS units to provide other services such as alarms, status control, and system updates. The design takes into consideration important factors regarding both position and data communication. Thus, the project integrates location determination (GPS) and cellular (GSM) – two distinct and powerful technologies in a single system. VMSS is based on a PIC microcontroller-based system equipped with a GPS receiver and a GSM Module operating in the 900 MHz band. We housed the parts in one small plastic unit, which was then mounted on the vehicle and connected to GPS and GSM antennas. The position, identity, heading, and speed are transmitted either automatically at user-defined time intervals or when a certain event occurs with an assigned message (e.g.; accident, alert, or leaving/entering an admissible geographical area). The GPS Module outputs the vehicle location information such as longitude, latitude, direction, and Greenwich Time every five minutes. The GSM wireless communications function is based on a GSM network established in a valid region and with a valid service provider. Via the SMS provided by the GSM network, the location information and the status of the GPS-GSM VMSS are sent to the control center. Meanwhile, the VMSS receives the control information from the control center via the same SMS. Next, the GPS-GSM VMSS sends the information stored in the microcontroller via an RS-232 interface. 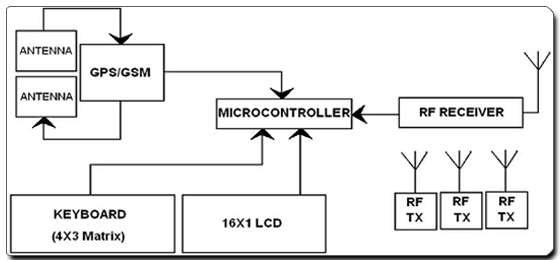
There are two ways to use the VMSS’ alarm function, which can be signified by either a buzzer or presented on LCD. The first way is to receive the command from the control center; second way is to manually send the alarm information to the control center with the push of a button. The base station consists of landline modem(s) and GIS workstation. The information about the vehicle is received at a base station and is then displayed on a PC based map. Vehicle information can be viewed on electronic maps via the Internet or specialized software. Geographic Information Systems (GIS) provides a current, spatial, visual representation of transit operations. It is a special type of computerized database management system in which geographic databases are related to one via a common set of location coordinates. STAGES OF VMSS STAGE 1:
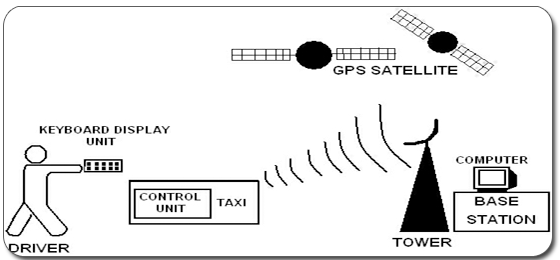
STAGE 2:
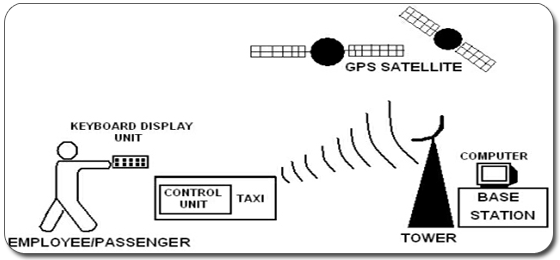
STAGE 3:
STAGE 4:
STAGE 5:
|
|
New IT failure research and statistics Project size: The average project size reported by the survey is about $5.5 million. (See notes below for discussion of project size.) Success and failure metrics: In general, the simplest definition of failure consists of projects that are late, over-budget, or do not deliver planned benefits. The following diagram tells this part of the story for 2009 and 2010: 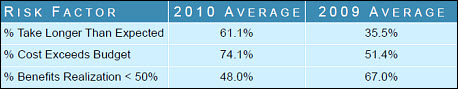
We see a dramatic increase in late and over-budget projects in 2010, as compared with 2009. Significantly, survey respondents reported improved achieving a higher level of expected benefit than in the prior year. One interpretation of this data suggests that companies prioritized project results over maintaining the budget or schedule plan. While that’s a positive sign, the survey commentary points out these numbers also indicate that executives did not plan their ERP implementations in a sufficiently realistic manner. These results definitely show good news and bad mixed together. Although the report does not supply sufficient data to draw any conclusions on this point, it would be useful to correlate implementation rollout approach with budget or schedule overruns. 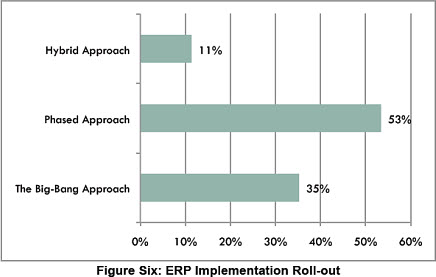
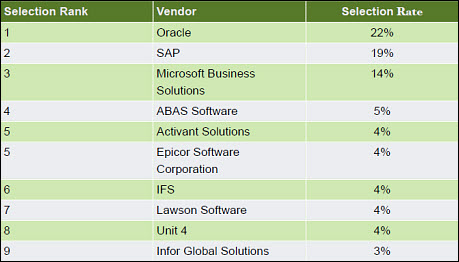
The diagram also shows that some implementations use a hybrid rollout, which incorporates both phased and big-bang for different parts of the system. Customizations: ERP customizations can add complexity to implementations, increasing project cost and risk. In addition, customized code can make downstream upgrades more difficult and expensive. Despite these risks, only 15% of survey respondents installed “plain vanilla” software without any customizations. Vendor selections: The following table shows the vendors that survey participants chose for their implementations; Oracle, SAP, and Microsoft top the list:
STRATEGIC ANALYSIS The Panorama study is a useful indicator for understanding success and failure on ERP projects. For that reason, we must commend Panorama for its research contribution.Article Source |
|
|
GREEN COMPUTING Your computer Chances are you spend the majority of your day sitting in front of the keyboard, and a few small changes can go a long way toward reducing its negative impact on the environment. As an added bonus, doing your part for the environment will save you money, too. This Earth Day, we've rounded up a few simple ways you can go green with your computer. Shutdown Your Computer Without Losing the Perks of an Always-On PC Obviously, computers require electricity to run, so shutting down, sleeping, or hibernating your computer when you're not using it conserves energy. Every modern operating system has its own settings for conserving power, so the first thing you should do—if you haven't already—is open the power settings of your computer and set them for optimal energy use. Set your computer to put your monitor to sleep, spin down your hard drives, and put your computer to sleep when you're not using it. Even better, since your computer uses less power when hibernating than when sleeping, set up your computer to hibernate rather than just go to sleep. One of the biggest turn-offs (no pun intended) about shutting down or sleeping your computer is that you miss out on some of the finer things your computer provides even when you're away. For example, if you're downloading a large file, you may want the download to continue even when you're away. Likewise, we've covered tons of ways toremotely access your computer, all of which no longer work if your computer's turned off. Luckily you can continue using your computer during these times but still conserve power the rest of the time. 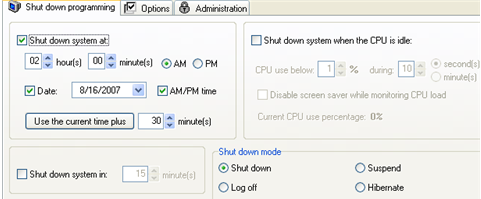
For example, Windows users should check out previously mentioned WinOFF, which shuts down, restarts, and hibernates your computer (among other things) after a certain amount of time, at a specific time, or when your CPU goes idle so that your computer automatically shuts off at times you don't need it. 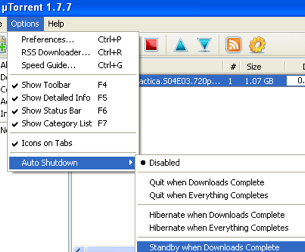
If a download is what you're waiting for, many peer-to-peer clients, like the popular BitTorrent client uTorrent, can shutdown your computer when a download completes so you can get your file and save energy, too. Between WinOFF and built-in shutdown features common to many apps, we've taken care of the the download problem—but what about when you want to access your computer remotely? If it's shut down, you can't very well get to it, can you? Actually, you can, assuming you set up Wake-on-LAN on your computer. Once Wake-on-LAN's enabled, you can turn your computer on over the internet from anywhere—so there's no reason not to shut down your computer when you leave the house. Finally, if you're on a Mac laptop, check out previously mentioned SmartSleep to enhance your power-saving options. Save Paper when Printing When it comes to the environment, one of the first places most offices can improve is the giant pile of discarded paper by the network printer. Aside from obvious things you can do on your own—like printing duplex, printing to PDF, previewing before printing, and not printing hundreds of copies of an email forward to plaster around the office—there are a few other tools you can use to minimize wasting paper and ink when printing. To save ink and paper when you're printing from your browser, use previously mentioned Firefox extension Aardvark to tweak the layout of a page and remove elements—like ads and images—that you don't need on the printed page. 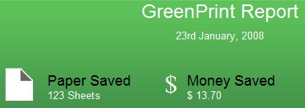
When you're not printing from the browser, Windows users can save tons on ink and paper with previously mentioned GreenPrint, a freeware application that automatically identifies and removes unnecessary pages or space from your printouts before they head to the printer. If you're regularly sending documents back and forth to other people or businesses, you can also save a few trees and save a little time in the process with a couple of office hacks. For example, rather than going through the age-old print, sign, and fax dance handed down through the generations by our forefathers, try creating a scanned signature and then sending scanned PDFs rather than faxes. It's quicker and it saves on resources and costs. Turn Off Peripherals to Kill the Vampires Now that you've put good energy practices into use on your PC, it's time to move onto the power-hungry peripherals you've got plugged into it. Whenever possible, you want to turn off any peripheral when you're not using it—like your printer or monitor. Likewise, you should be aware of any gear in your computing setup that draws standby power (a.k.a., vampire power) even when you've turned off the device in question. Vampires commonly stand out as large, unsightly AC adapters. 
While you could diligently unplug your wall warts or keep them plugged into a power strip that you switch off when they're not in use, you can go even further and automate the process with gadgets like the Energy Saving Smart Strip (original post) and the Power Minder (original post), both of which monitor your PC's power state and automatically shut down other peripherals when you turn off your computer.For more on saving energy at your computer, check out our top 10 computing energysavers. Estimate Your Power Usage 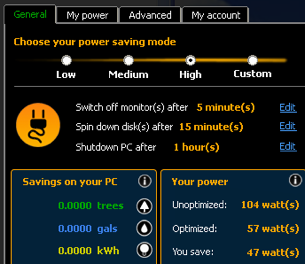
It's one thing to know your computer sucks down a lot of energy every month, but actual power usage numbers drives the point home. Windows can install previously mentioned LocalCooling, an tool that both helps you tweak your Windows power saving settings and visualize the amount of power your computer consumes. Some users reported inaccurate measures with the app when we first posted about it, but the well-intentioned LocalCooling team continues in their efforts to improve the application and help you save energy and visualize the impact of your energy-saving. If LocalCooling's not giving you accurate results or you want to get a more definitive look at your PC's power consumption, regardless of your operating system, this Coding Horror post demonstrates in detail how to determine and lower the cost of leaving your PC running (original post). Article Source
|
|
|
Win-win communication not only fosters understanding, affirmation, validation and appreciation, but it also creates an atmosphere of trust, honor and respect. When someone truly listens to you, don't you feel special? Listening well is a two-way street, and to be effective communicators, we must all listen well to each other. One-way listening can be equated to driving down a one-way street the wrong way. It's dangerous, it can get you into trouble and it can be expensive, as illustrated in the following example. Sam, a dispatcher for a national moving company in Philadelphia, gave Mike, a new driver, an assignment to go to Portsmouth to make a household goods delivery. When Mike arrived in Portsmouth, he called Sam for further instructions. As Sam gave Mike the necessary information, Mike got a strange feeling that something wasn't quite right. Mike asked Sam for the complete address, which was Maple Street in Portsmouth, Virginia. Well, Mike was in Portsmouth, but it was Portsmouth, Rhode Island. Mike was ten hours away from where he was supposed to be. He had traveled north in the wrong direction. Not only did this cost the company time and money, but also the owner of the goods was not pleased. What caused this expensive mistake? Ineffective listening by both parties. In his haste, Mike didn't listen to all the information that Sam gave him, and Sam neglected to get accurate acknowledgment from Mike stating that he understood the instructions.
Listening well is a skill that requires practice. .jpg)
To be effective when interacting over the telephone, hone your verbal skills and focus completely on what the speaker is saying. Listen closely to your intuition. The best example of this is to observe how blind people communicate. Since they do not have the gift of sight, they focus on their other gifts and develop them. Their hearing is acute, and they can people read by focusing on a person's voice attitude and the words that the person uses. Those of us whose work depends on the telephone should do the same.
A good listener, both on the telephone and in person, will: 
A poor listener, both on the telephone and in person: 
Remember that effective listening can open many doors. If you listen with your eyes, your ears and your mind, you will always get the information you need. Article Source |
|




 The Art Of Listening
The Art Of Listening